Integration Spotlight: Smarter Security Operations with Microsoft Sentinel + Observo AI

Microsoft Sentinel is a popular cloud-native SIEM, offering tight integration across Azure services, native machine learning models, and the scalability of Microsoft’s cloud infrastructure. It enables real-time threat detection and response across hybrid environments, making it a go-to solution for many enterprises embracing the Microsoft ecosystem.
But like all modern SIEMs, Sentinel is only as effective as the data it ingests. As cloud workloads scale and telemetry grows exponentially, customers face rising costs and operational complexity. That’s where Observo AI adds powerful value.
Observo AI delivers AI-native telemetry pipelines that enhance Microsoft Sentinel by reducing noise, enriching events, and optimizing routing before data hits the SIEM. This results in lower infrastructure overhead, faster detection, and more actionable insights.
Let’s take a closer look at how Observo helps Sentinel users achieve more complete security operations—without breaking the budget.
Where Sentinel Shines
Microsoft Sentinel offers seamless integration across Microsoft’s cloud ecosystem, including Azure Monitor, Microsoft Defender, and Microsoft 365. This deep connectivity allows security teams to unify signals from across their infrastructure and act on them with greater speed and accuracy. Sentinel also includes built-in analytics rules for real-time correlation and threat detection, helping organizations identify and respond to incidents faster.
Its consumption-based pricing model makes it an attractive option for teams looking to scale without upfront licensing constraints. Sentinel also supports hybrid and multicloud environments, making it a flexible choice for enterprises operating across on-prem, Azure, AWS, and beyond.
Scaling Sentinel Without Drowning in Data
But as organizations scale their cloud infrastructure and security tooling, challenges begin to surface—particularly when it comes to managing the growing volume and variety of telemetry data. Logs from virtual machines, custom applications, firewalls, and third-party SaaS tools can generate terabytes of data daily. Feeding all of this directly into Microsoft Sentinel without filtering or optimization quickly becomes cost-prohibitive, as every gigabyte ingested drives up Azure Monitor and Sentinel-related expenses. The more data you push in, the more strain you place on your SIEM budget.
Beyond cost, there’s also the challenge of usability. Many log sources—especially custom applications or legacy systems—produce telemetry that doesn’t conform to Sentinel’s schemas. Without normalization, that data is difficult to parse, visualize, or correlate using KQL, rendering it far less valuable for investigations or dashboards. This forces teams to spend valuable engineering time building and maintaining custom parsers or transformation logic just to make the data actionable.
Finally, because most of the enrichment happens downstream within Sentinel itself, analysts often have to rely on complex queries to add basic context like geolocation, identity mapping, or threat intel. This increases query complexity, slows performance, and puts added pressure on detection rules. In effect, Sentinel is being asked to do too much—processing raw, noisy data while also being the brain of your security operations. Without smarter upstream optimization, this model becomes unsustainable at scale.
Observo AI Pipeline: Smarter Ingestion for Sentinel
Observo AI offers a smarter ingestion layer that complements Microsoft Sentinel. Instead of sending raw logs directly into Azure, Observo filters, enriches, and routes telemetry in real time—dramatically improving data quality and cost efficiency.
With AI-powered log reduction, Observo identifies and filters out low-value or redundant logs before ingestion, cutting volume by up to 80%. This significantly lowers storage and processing costs while ensuring that only actionable data reaches Sentinel.
Observo also delivers out-of-the-box normalization by applying schema mapping and Grok-pattern recognition to unstructured logs. This allows data from custom or non-standard sources to be transformed into Microsoft-compatible formats without manual intervention.
To enhance detection capabilities, Observo performs inline enrichment by appending threat intelligence, geo-IP details, and identity metadata upstream. This adds critical context before data hits Sentinel—without increasing the burden on KQL queries.
Finally, Observo offers flexible routing options that let you send high-signal logs to Sentinel in real time while offloading compliance-only or archival data to Azure Blob Storage or other cold tiers. This tiered approach improves cost control without sacrificing visibility.
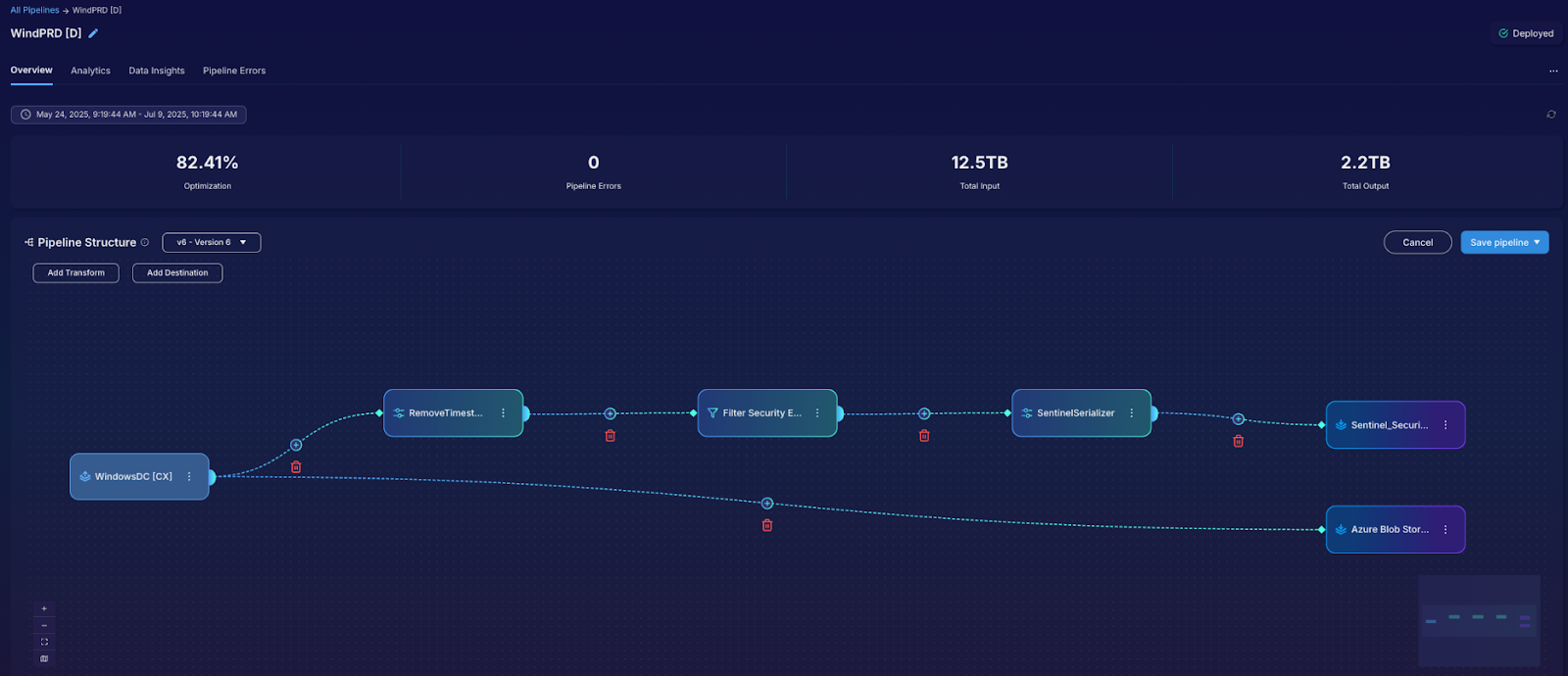
Streamlined Data Collection with Observo Edge Collector
Instead of deploying and managing dozens of agents across your environment, Sentinel customers can use the Observo Edge Collector to unify and simplify log collection.
Observo Edge Collector supports source-agnostic collection across your entire stack. It can ingest telemetry from Azure virtual machines, AWS EC2 instances, Google Cloud services, Kubernetes clusters, firewalls, and even SaaS applications—without needing custom agents.
It also provides edge-side optimization, allowing you to filter, enrich, and normalize data right at the point of collection. This minimizes unnecessary transmission, reduces cloud egress charges, and ensures that only high-value, context-rich data reaches Microsoft Sentinel and other downstream systems.
With multi-destination support, the Edge Collector can send processed data to multiple tools in parallel. For example, the same filtered log stream can be routed to Microsoft Sentinel for real-time analysis, to Azure Monitor for infrastructure visibility, and to long-term cloud storage for compliance and forensics—without duplicating ingestion costs.
Data Tiering and Rehydration with Observo Query
To balance cost and visibility, Observo Query lets you intelligently route and retrieve data based on business value. You can send real-time, high-signal logs directly to Microsoft Sentinel for dashboards, alerts, and investigations. This ensures your SecOps team always has access to the most actionable data—without sifting through noise.
Meanwhile, low-priority logs can be archived in Azure Blob Storage or another object store for long-term retention. These logs remain available for compliance, audit, or forensics—without driving up hot storage or SIEM ingestion costs.
If you need those archived logs later, you can query and rehydrate them on demand through Observo. This gives SOC teams the flexibility to investigate historical incidents or support compliance reviews without keeping every log in hot storage.
Enabling Long-Term Compliance and Retention in Azure
Security teams often need to retain logs for years, but storing everything in Sentinel’s active tier drives up costs fast. Observo AI integrates with Azure Blob Storage to create a cost-effective, compliant data lake for long-term retention.
These archives are audit-ready, preserving full-fidelity logs to meet standards like HIPAA, PCI DSS, and SOC 2. Observo maintains structure and integrity for easy access during audits or investigations.
Logs remain searchable via Observo Query, so analysts can run queries on cold data without rehydrating it into Sentinel. This provides historical visibility without incurring costs associated with SIEM indexing and egress. Observo also keeps your data secure and scalable with built-in RBAC, encryption, and multi-region replication. It’s designed to meet enterprise-grade governance from day one.
Making Microsoft Sentinel Better with Observo AI
Observo AI enhances Sentinel environments with:
- Massive log reduction: Smart summarization cuts data volumes by over 80% before they hit your Azure ingestion pipeline
- AI-native automation: Replace hand-written regex and manual rules with optimization pattern detection and schema alignment that evolves with your data
- Faster MTTR: sentiment-enriched logs help analysts act faster with less noise
- Flexible routing: Tier data based on business value and destination for faster queries and reduced storage and compute costs
Better Together: Microsoft Sentinel + Observo AI
Whether you're just starting with Sentinel or expanding with new log sources and analytics tools, Observo AI helps you get more value from every log. With smart summarization for reduced log volume, flexible data routing, and data tiering automation, your SOC gains better visibility and faster threat response.
Download the CISO Field Guide to AI Security Data Pipelines to learn how modern teams are using Observo AI to supercharge Microsoft Sentinel—and secure more with less.




