How AI-Native Data Pipelines Accelerate Threat Hunting

The Importance of Finding Threats Before They Turn Into Something Serious
Every security incident starts as a small signal: an unusual connection, a mistyped command, or a subtle change in behavior. The challenge is that most of these signals are buried in mountains of noise. Modern SOCs process terabytes of telemetry each day, but only a fraction contains real indicators of compromise. Without intelligent detection and prioritization, valuable warning signs get lost in the flood of low-value events.
That is where threat hunting proves its worth. Instead of waiting for alerts to fire, proactive teams look for subtle anomalies and behaviors that hint at an attack in progress. But even the best hunters can only work with the data they can see, and when logs are noisy, incomplete, or slow to query, early detection becomes nearly impossible.
If SOC analysts are spending time fixing data quality and ingest instead of hunting threats, they lose critical hours each day. Many teams still rely on manual schema mapping, custom collectors, or static filters just to keep data flowing efficiently into their SIEM. Ensuring that each source is parsed, normalized, and optimized so it does not trigger ingest limits requires constant data engineering effort. Each cycle spent reshaping or tuning data means less time for proactive defense, leaving organizations more reactive and vulnerable when incidents occur.
The ability to identify anomalies in motion, before they ever reach the SIEM, can make the difference between quick containment and a full-blown breach. By enriching telemetry as it is ingested and flagging high-risk patterns in real time, organizations can stop threats in their earliest stages long before they escalate into incidents that consume weeks of remediation effort.
When Too Many Alerts Look the Same, Real Threats Get Missed
Security and DevOps teams are overwhelmed by a constant flood of alerts. Each one demands attention, yet most represent repetitive, low-value events. Without the right context or prioritization, everything appears equally urgent. Analysts spend valuable time chasing false positives while real threats slip by unnoticed.
The core issue is not a lack of data but a lack of differentiation. When every alert looks identical, even experienced analysts struggle to identify what truly matters. Teams end up reacting instead of investigating, reviewing thousands of events manually and losing precious time that could be spent on higher-value analysis.
This cycle leads directly to alert fatigue. Analysts tune out noise to stay sane, and in doing so, risk missing the rare anomalies that signal a real attack. Visibility declines, response slows, and adversaries gain more time to move laterally and escalate privileges inside the environment.
How AI-Native Pipelines Change the Equation
Traditional pipelines passively move data from source to destination. They rely on static rules, regex filters, and manual field mappings to shape logs before analysis. While that approach works for predictable data, it cannot keep pace with modern, high-volume environments where new data types, behaviors, and threats appear daily.
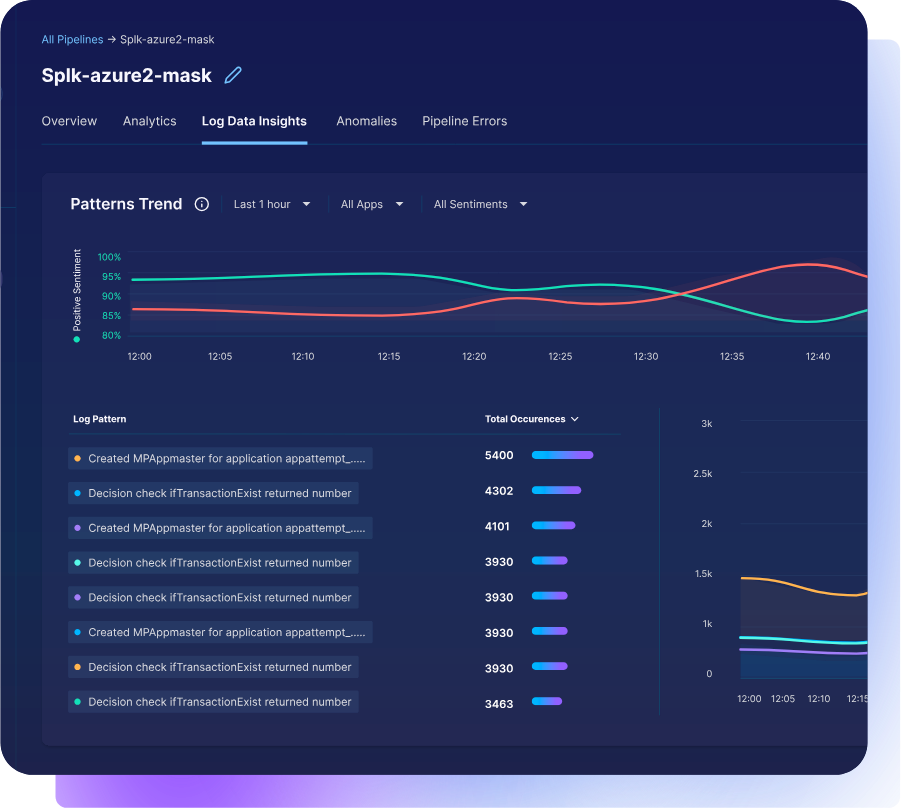
AI-native pipelines take a fundamentally different approach. Instead of waiting for data to reach the SIEM or analytics platform, they analyze it in motion. Machine learning models identify patterns, group similar events, and detect anomalies before indexing occurs. This allows the system to highlight unusual activity the moment it appears, not hours later during manual review.
AI-powered parsing and Grok pattern generation also eliminate weeks of manual schema work. The pipeline continuously learns the structure of new log types and automatically maps them into normalized schemas. As a result, data becomes usable faster, and analysts can investigate patterns instead of maintaining parsers.
Because these pipelines understand relationships across users, assets, and behaviors, they can apply context directly to the data stream. Events are enriched with threat intelligence, geolocation, and historical baselines to determine which alerts deserve immediate attention. The outcome is a continuous, adaptive flow of clean, enriched telemetry that strengthens every downstream security tool.
What Observo AI Delivers
Observo AI helps security teams move from reactive alert handling to proactive threat hunting. By analyzing data in motion and applying AI to prioritize what matters, the platform dramatically reduces noise and accelerates detection.
Observo cuts mean time to respond (MTTR) by 40% or more by eliminating alert fatigue. Instead of chasing hundreds of duplicate or low-value notifications, analysts receive clear, context-rich alerts that show which threats require immediate action. With fewer distractions and faster access to high-signal data, investigations begin sooner and resolve faster.
Observo also reduces noisy, distracting data by more than 80% before it ever reaches the SIEM. Machine learning models identify repetitive, low-risk events in real time and filter them out, ensuring only relevant and enriched telemetry is analyzed downstream. This allows teams to spend less time on triage and more time on strategic defense.
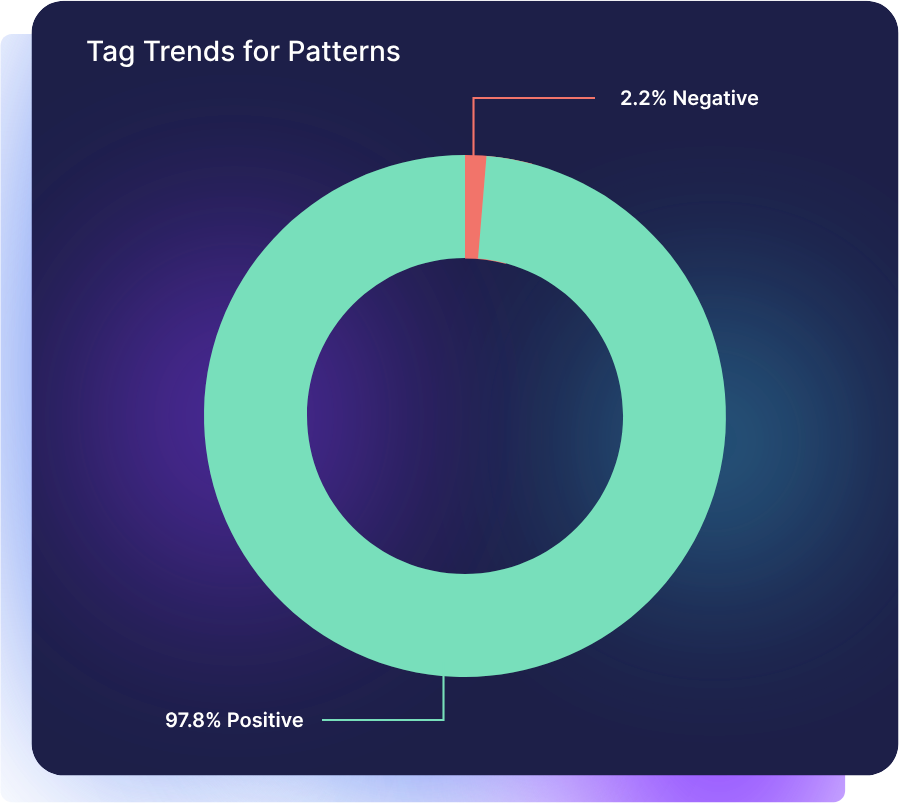
Finally, the platform uses AI-powered sentiment analysis to score and prioritize alerts based on risk and behavioral context. Events that resemble known attack patterns or show signs of lateral movement are automatically elevated, while low-confidence or routine events are de-emphasized. This scoring system keeps analysts focused on the alerts that matter most and minimizes the chance of missing a genuine threat.
Together, these capabilities help SOC teams streamline investigations, increase accuracy, and strengthen overall security posture. By turning overwhelming volumes of telemetry into streamlined insight, Observo AI gives analysts back the time and clarity they need to hunt threats effectively before they start to impact the business.
Real-World Example: A U.S. Bank Reduces Noise and Accelerates Threat Detection
One of the largest retail banks in the United States faced a growing visibility problem. Their SOC was flooded with alerts generated from 20 terabytes of daily security data spanning multiple cloud environments. Analysts were buried under repetitive, low-value events, making it nearly impossible to identify anomalies that could indicate emerging threats.
To regain control, the bank deployed Observo AI as the foundation for its modern security data pipeline. Within weeks, the platform filtered and transformed data in motion, reducing overall volume by 70% before it reached the SIEM. High-signal events were enriched, scored, and routed in real time, while routine traffic was automatically deprioritized, summarized, or archived. The result was a faster, leaner, and more intelligent data stream that allowed analysts to focus on investigation rather than noise or data wrangling.
By removing low-value data and surfacing enriched anomalies, the bank not only reduced false positives but also accelerated mean time to detection and response by more than 40%. What had once taken hours of manual correlation could now be recognized and prioritized in seconds.
“Before Observo AI, our analysts spent too much time sorting through noise and manually correlating events. Now, high-risk anomalies surface automatically, and we can focus on investigation instead of triage. It has completely changed the pace of detection in our SOC.”
— VP, Security Operations, Top 15 U.S. Bank
Accelerate Threat Hunting to Secure Your Enterprise
Faster detection means stronger defense. Observo AI helps SOC teams cut through noise and focus on the threats that matter most. By filtering low-value telemetry, enriching data in motion, and prioritizing alerts through AI-driven sentiment analysis, organizations can detect and respond to threats up to 40 percent faster. With clearer visibility and more accurate context, your analysts can stay ahead of attackers and protect your enterprise with confidence.
Find out for yourself. Request a demo with our engineers to see how Observo AI can help your team detect threats faster, cut alert fatigue, and focus on securing your organization.




